On August the 17th, the Maltego Academic and Non-Profit Research Program had the great pleasure to host a webinar on “How Technology Changed Investigative Journalism”. Our guest speakers Aida and Brian guided us through the thrilling journey of three recently developed journalistic investigations empowered by Maltego.
The webinar discusses:
- A delve into the research of two journalists who are using technology in critically important exposes.
- How they collect data, where they collect data and ways in which data can be processed and used.
- How to safeguard the integrity of the investigator in both the digital and physical worlds.
- The ethical question that governs journalism.
- Expose the Maltego community to knowledge from a journalist’s investigative perspective.
- The importance of what happens after articles are published on sensitive topics.
Let’s take a look at what has been shared!
Human-trafficking in prostitution across Europe: A Person of Interest investigation 🔗︎
Aida Kokanovic has fallen in love with investigative journalism through investigation of corruption and drug crimes. Her career goal is to catch some bad guys and make OSINT tools accessible and applicable for all investigative journalists.
She is in the process of finishing her master’s degree in journalism and social studies at Roskilde University in Denmark and currently works at Danish Broadcast Organization as an investigative journalist.
In a truly vivid way, Aida opens the webinar by narrating the heartbreaking case of “Sofia”, a young woman in her early twenties, who finds herself amid difficult circumstances. Unemployment, a partner with substance abuse problems and financial difficulties. In her quest to improve her situation, Sofia comes across an online advertisement promising thousands of Euros per week, good working conditions, and access to social services. She will work as an escort. As the ad suggests, she will be able to choose her own clients. After her partner’s approval, Sofia decides to take the job. Two men drive her from Poland to Denmark. Instead of a luxurious home, Sofia is constantly moved from one illegal brothel to another. The payment she receives is the minimum necessary to survive while she has no say over the clients she will have sex with, and her passport is withheld.
After this brief but clear introduction on how the operational processes of human trafficking networks usually look like, Aida walked us through her research, the data she gathered, and how she used Maltego for this investigation.
A starting point of the investigation was gathering of information in sex recruiting ads, aiming to test the hypothesis that women are moved across Europe. One of the main goals of the project is to detect organized human trafficking networks in sex work across Europe.
This is where OSINT comes into play. Aida performed a contact exploitation investigation. What does this mean? It means getting as much information as possible from a single phone number or a single email provided by one of the suspects in the recruiting advertisement. After gathering all this information from many phone numbers and email addresses, she performs a link analysis to detect connections between the suspects.
Below is a diagram of the complete workflow of her investigative techniques:
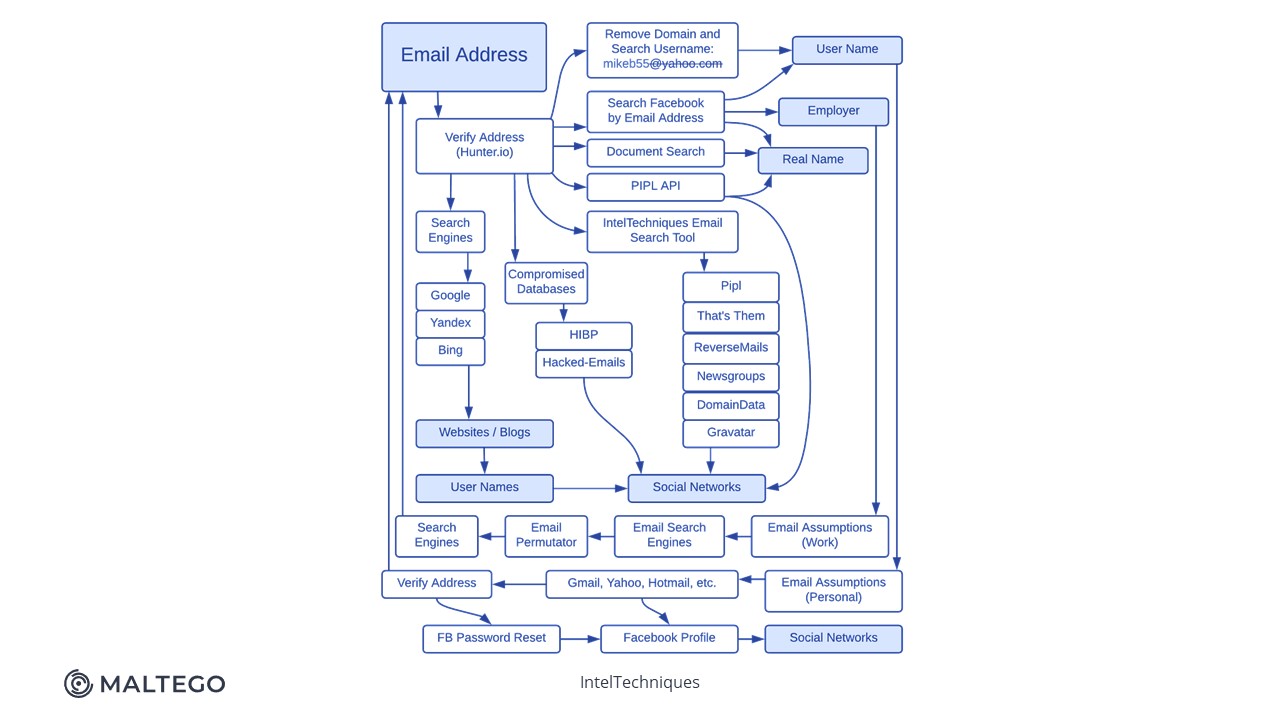
Aida got a lot of data from connecting the contacts on her burner phone to apps and social media. She pointed out that it was quite challenging to have a full overview of hundreds of names, pictures, and nicknames while keeping up with every tab on her spreadsheet. She populated her graph with her existing information and combined it with a trial access to ShadowDragon Transforms in Maltego. In her own words, the fireworks started.
She isolated about 50 Entities and ran the Bulk Search Transform at the same time on all the Entities, and in matter of minutes, almost all the information that she had on her burner phone appeared on her screen. Maltego empowered her investigation by making every link and connection visible and apparent. It also gave her extra data that she didn’t have on her burner phone before.

During her presentation, Aida showed us the techniques that she used in addition to Maltego during her research. For example, how to create a persona to ensure that nothing you used during your research is traced back to you.
The whole process includes some quite interesting tips and tricks:
- Cool hacks such as how to create and use a sock puppet in combination with a burner phone to connect social media and virtual life and collect information.
- How to protect your identity to investigate safely.
- How to play with hacks in different apps to get the most information out of a target.

OSINT + GEOINT for Human Rights Investigations 🔗︎
Following Aida’s presentation, Brian Perlman gave a very impressive presentation on the use and combination of open-source intelligence (OSINT), geospatial intelligence (GEOINT), and the use of investigative tools for two use cases:
- An eight-month long investigation pertaining the 44-day war in Artsakh
- An investigation of a protest in Sudan

Brian is an open-source intelligence and geospatial intelligence analyst with a focus on international human rights violations. He holds a master’s degree in journalism from the University of California, Berkeley, and worked as a manager at the Human Rights Center at Berkeley Law, where he led a team of student researchers investigating attacks on Syrian healthcare infrastructure.
First, he encouraged all digital OSINT Investigators to check out the Berkeley Protocol on Digital Open-Source Investigations and to Digital Witness: Using Open Source Information for Human Rights Investigation, Documentation, and Accountability. This is especially useful for people who do not have a legal background, as both readings can give a broad look at Ethics regarding OSINT.
For the first example, the Nagorno-Karabakh Investigation, his remarks on what they did for the investigation were on:
- Conflict damage assessment + Weapons ID
- Geolocation/Chronolocation
- Digital content preservation + archiving
- Satellite imagery discovery + analysis
- Facial comparison
- Uniforms ID
For the Sudan case, the research focused on:
- Geolocation/Chronolocation
- EXIF data extraction + analysis
- Digital content preservation + archiving
- Audio comparison;
- Forensic video analysis (FVA)
Brian and his team identified weapons by comparing social media images and imagery reports. He pointed out how different tools available in Maltego, like ShadowDragon or VirusTotal, are very powerful while you are conducting this type of research.
During his presentation, he also shared his top go-tools, besides Maltego, to increase his security and protect his privacy thorough the research process, but also to empower his investigation:
- Combining Social Media Imagery with different OSINT tools. He used the example of PeakVisor, tool that is usually used by hikers, but by comparing the topography, the team was able to determine the exact location of where the damage happened.
- Brian recommends the use of Hunchly for internet content preservation in combination with YouTube-DL for video preservation. Later they archived all the information on Mega.
- To avoid accessing Telegram from his own machine, and in combination with archiving tools, Brian recommended the use of VMWARE to search for the origin from a virtual machine.
- Comparing the audio of the same incident from different perspectives, to be able to get a fuller picture of what was going on.

Both speakers agree on three things:
- The safety and success of an investigation or operation itself begins with the safety of the investigator. During the webinar, both share with the audience useful tips to achieve this goal.
- Being able to automate investigation processes takes away a lot of roadblocks. Maltego was instrumental in data management and analysis. Not only did it considerably reduce the research time, but it also made the key elements of the investigation evident.
- The financial component poses significant constraints to the development of an investigation. These can be overcome through dialogue and the establishment of partnerships that support and encourage investigative journalism.
Check out the entire webinar now to take note of all these practical guidelines and detailed use case demonstrations!
Don’t forget to follow us on Twitter and LinkedIn and sign up for our email newsletter to stay updated on the latest news, tutorials, and events.
Happy investigating!